Docker Jitterbit private agent automatic registration tutorial
Introduction
This tutorial shows you how to set up two (or more) Docker private agents that will automatically register to a designated private agent group in your organization. You do this using a register.json file.
Note
Additional Docker private agent documentation is available at https://hub.docker.com/r/jitterbit/agent/.
Overview
To complete this tutorial, complete each step in order:
-
Prerequisites: Make sure that you have the necessary software, credentials, and available agents.
Important
If using agents version 10.83 / 11.21 or later, skip steps 2 and 3 when using an Agent registration access token as a recommended prerequisite. Steps 2 and 3 should be completed only if you are using Harmony credentials in the
register.jsonfile. -
Create an agent installer user: If not using an Agent Registration access token, create a username and password that will be shared between agents and used when registering.
-
Generate an encrypted username and password: If not using an Agent Registration access token, generate encrypted versions of the username and password.
-
Choose an agent group: Select an agent group and obtain its ID.
-
Create the
register.jsonFile: Create, complete, and install theregister.jsonfile. -
Launch the first agent: Launch the first agent using the automatic registration that you have configured.
-
Launch the second agent: Launch a second agent using the same automatic registration that you have configured.
-
Confirm two running agents: Check that both of the agents have been started by using the Jitterbit Management Console.
Bonus Exercise: Instead of using a shared register.json file, configure and start an agent using environment variables whose values can be shared.
1. Prerequisites
To complete this tutorial, you will need:
- Docker (1.12 or higher) on Windows, Linux, or macOS
- A Harmony organization and login with Admin permission
- A minimum of two available agents in your Harmony subscription
If using agents version 10.83 / 11.21 or later, we recommend using Agent registration access tokens over encrypted Agent Installer user credentials. Agent Registration access tokens do not expire and can be managed in the Management Console at any time.
2. Create an agent installer user
Important
If using agents version 10.83 / 11.21 or later, skip this step when using an Agent registration access token as a recommended prerequisite. This step should be completed only if you are using Harmony credentials in the register.json file.
Create a user in your Harmony organization that has only the Agent Install permission:
-
Log in to the Harmony portal (https://login.jitterbit.com) as a user with Admin permission (administrator credentials).
-
Go to Management Console > Organizations.
-
Add a new role and name it Agent Installer:
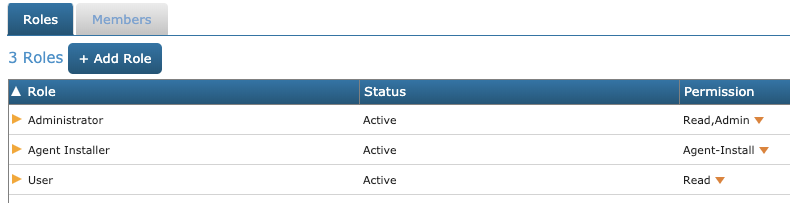
-
Modify this new role's permissions by using the dropdown next to Read to select only the Agent Install permission:
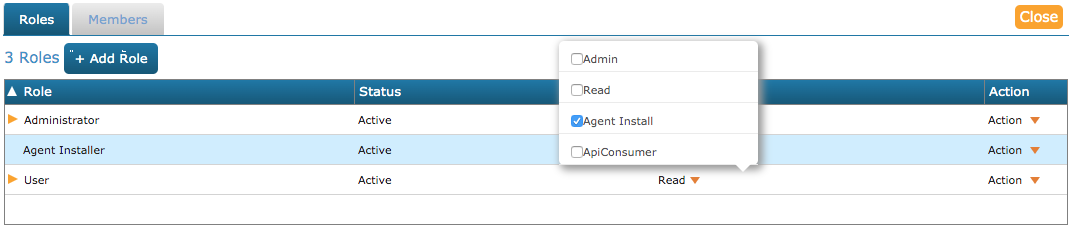
-
Select the Members tab, add a new member using a valid email address, and assign it to the Agent Installer role:
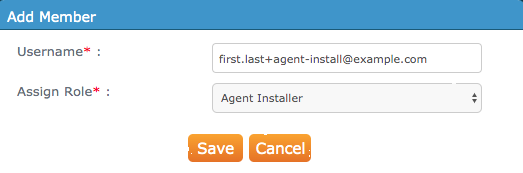
Note
This should be a dedicated user account with a valid email address. This will be used specifically for automatically registering agents.
-
Log out of the current user account (the one with Admin permission). This enables you to respond to the email for the new user you just created. Otherwise, you will need to respond using a private browser window to prevent using any cached login credentials.
-
Register this new user (check its email for the activation steps). You will need the username and password you created in step 3, Generate an encrypted username and password.
-
Once the new user has been successfully registered, you can log back in to the Harmony portal using your administrator credentials.
3. Generate an encrypted username and password
Important
If using agents version 10.83 / 11.21 or later, skip this step when using an Agent registration access token as a recommended prerequisite. This step should be completed only if you are using Harmony credentials in the register.json file.
Generate an encrypted username and password for the dedicated user you just created for automatically registering agents:
-
From a command line in a terminal running Docker, encrypt the username (shown below as
first.last+agent-install@example.com) and password (shown below assome_Passw0Rd1) of the member you just created:# This Docker command returns an encrypted username and password (example only, actual will be different) docker run --rm jitterbit/agent:latest jitterbit-utils -e 'first.last+agent-install@example.com' 'some_Passw0Rd1' $000jwdBLiBsJnx4hCNIob1yn3gK9kisBm6knxmLFxV.../WHp6X7pvBkxuROg== $00phLWHm04Zsx9Wmug1eiIVaJemGjjm91CAVtkHH0bG+Y= -
The encrypted credentials are on the two lines following the command. Note these will be different each time they are generated, even with the same username and password. The username is followed by the password:
- Encrypted username:
$000jwdBLiBsJnx4hCNIob1yn3gK9kisBm6knxmLFxV.../WHp6X7pvBkxuROg== - Encrypted password:
$00phLWHm04Zsx9Wmug1eiIVaJemGjjm91CAVtkHH0bG+Y=
- Encrypted username:
Caution
If you escape the username or password in the Docker command, check that value returned by the escape command matches correctly. This can be tricky:
# Escaping special characters in 4pete'sSake!
echo "4pete'sSake\!"
4pete'sSake\!
echo '4pete'"'"'sSake!'
4pete'sSake!
4. Choose an agent group
Choose an agent group in your org and note its ID:
-
Go to Management Console > Agents.
-
Note the agent group name and ID.
5. Create the register.json file
Create the file for automatically registering the agent:
-
In your current working directory, create a folder called
conf. -
In that directory, create and edit a file called
register.json. -
Insert the cloud URL, token (or encrypted username and password), and agent group ID appropriate for your Harmony region:
Region Cloud URL NA (North America) https://na-east.jitterbit.com APAC (Asia-Pacific) https://apac-southeast.jitterbit.com EMEA (Europe, Middle East, Africa) https://emea-west.jitterbit.com Here is an example of a
register.jsonfile completed for use in the NA region:Important
Agent registration access tokens require agents version 10.83 / 11.21 or later.
register.json{ "cloudUrl": "https://na-east.jitterbit.com", "token": "jb_a1b23c45-d6ef-789a-b0cd-e12fabcd3e4f", "agentGroupId": "224281", "agentNamePrefix": "auto_%ip%_%host%_%guid%", "deregisterAgentOnDrainstop": "true", "retryCount": "10", "retryIntervalSeconds": "5" }Important
If using agents version 10.83 / 11.21 or later, we recommend using Agent registration access tokens over encrypted Agent Installer user credentials. Agent Registration access tokens do not expire and can be managed in the Management Console at any time.
register.json{ "cloudUrl": "https://na-east.jitterbit.com", "username": "$000MTF/XSfev/KjlB/M1Q5vFkPLBKU5.../PwoHRiSGGLlJ", "password": "$006WIdHtws7wrjgCNAoabUzu0f+HsyzAfAZtTpauvsHBE=", "agentGroupId": "224281", "agentNamePrefix": "auto_%ip%_%host%_%guid%", "deregisterAgentOnDrainstop": "true", "retryCount": "10", "retryIntervalSeconds": "5" }
6. Launch the first agent
Launch the first agent:
-
Make sure
<working directory>/confcontains the updatedregister.jsonfile. -
Go to your working directory, the parent to the
confdirectory. -
Use Docker to pull down the latest Jitterbit agent:
4. Launch a Docker private agent that uses thatdocker pull jitterbit/agent:latestconfdirectory and theregister.jsonfile:docker run -it --rm -v "$(pwd)/conf:/conf" jitterbit/agent:latest # Command returns: ffdb4ed859472029cbf0b1ef0d4259db5a6...7290e200d36dbe5f75bfb59349 -
The Docker name will show when you run the command
docker ps -a, and the container ID will match the value returned by theruncommand:docker ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS NAMES ffdb4ed85947 jitterbit/agent:latest "/entrypoint.sh /age…" 23 seconds ago Up 22 seconds bold_bhabha
Note
To stop or run the agent in background mode, use these commands:
-
To stop the agent, use
Control+Cordocker stop <docker-name>(You will need to note the Docker instance's container ID). -
To run the agent in background mode, use
-dwhen launching the agent:docker run -d --rm -v "$(pwd)/conf:/conf" jitterbit/agent:latest # Command returns: ffdb4ed859472029cbf0b1ef0d4259db5a6...7290e200d36dbe5f75bfb59349
7. Launch the second agent
Launch the second agent:
-
Make sure
<working directory>/confcontains the updatedregister.jsonfile. -
Go to your working directory, the parent to the
confdirectory. -
Use Docker to pull down the latest Jitterbit agent:
docker pull jitterbit/agent:latest -
Launch a second Docker private agent, substituting an appropriate name in this command for
<dockername>:docker run --name <dockername> -d --rm -v "$(pwd)/ conf:/conf " jitterbit/agent:latestTip
This time, we gave the Docker instance a
<dockername>so that you can stop it usingdocker stop <dockername>.
8. Confirm two running agents
Confirm that both the first and second agent are running:
- Return to Management Console > Agents > Agent Groups to confirm your running agents.
- You should see two agents running, each identified by a name based on the
agentNamePrefix, such asauto_172.17.0.2_b2a546cc080e_59a260ca_2020-02-14 17:43:03.033.
Environment variables
If using encrypted agent installer user credentials, you can also launch a container using environment variables instead of the register.json file.
Test using DOCKER_AGENT_NAME, AUTO_REGISTER, and AUTO_REGISTER__X_ environment variables:
DOCKER_AGENT_NAME=agent1
docker run -it --rm \
--name=${DOCKER_AGENT_NAME} \
-e AUTO_REGISTER="true" \
-e HARMONY_ORIGIN="https://na-east.jitterbit.com" \
-e AUTO_REGISTER_ENCRYPTED_USERNAME="<encrypted username>" \
-e AUTO_REGISTER_ENCRYPTED_PASSWORD="<encrypted password>" \
-e AUTO_REGISTER_AGENT_GROUP_ID="<agent group id>" \
-e AUTO_REGISTER_AGENT_NAME_PREFIX="auto_%ip%_%host%_%guid%" \
-e AUTO_REGISTER_DEREGISTER_ON_DRAINSTOP="true" \
jitterbit/agent:latest