Salesforce 3-legged OAuth 2.0 API security profile in Jitterbit API Manager
Introduction
Within a security profile, you can configure Salesforce as an OAuth 2.0 identity provider to provide API consumers access to an API using Salesforce authentication.
Note
This API security profile does not currently support 2-legged OAuth.
This page shows how to configure and use Salesforce authentication with a Jitterbit custom, OData, or proxy API by following these steps:
- Enable Salesforce as an identity provider
Configure the Salesforce instance as an identity provider. - Create a Connected App in Salesforce
Configure a Connected App in Salesforce and obtain the Salesforce Consumer Key (Client ID) and Salesforce Consumer Secret (Client Secret) that you will need to use as input for configuring a securing profile in API Manager. - Configure a security profile in API Manager
Configure and test Salesforce as the identity provider in API Manager. You will need to use the client ID and client secret obtained in the previous step. - Assign a security profile in API Manager
Assign the security profile to one or more Jitterbit custom, OData, or proxy APIs. - Access an API with Salesforce authentication
API consumers are able to use Salesforce authentication to consume Jitterbit custom, OData, or proxy APIs that the security profile is assigned to.
For additional information, see the Salesforce documentation Enable Salesforce as an Identity Provider and Authorize Apps with OAuth.
1. Enable Salesforce as an identity provider
Follow these steps to enable Salesforce as an identity provider in the Salesforce Classic UI:
-
Log in to the Salesforce instance as a Salesforce Admin.
-
In the Salesforce Classic UI, navigate to Setup > Administer > Security Controls > Identity Provider.
-
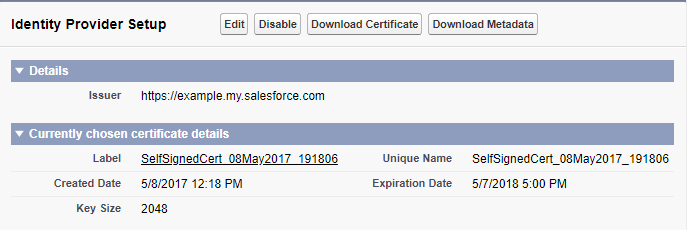
In the section Identity Provider Setup, verify that you have a domain name configured and that Salesforce is enabled as an identity provider:
-
If you do not have a domain configured, click the link to Configure a Domain Name and follow the steps to set up a domain and deploy it to users. This automatically enables Salesforce as an identity provider.
-
If you have a domain configured but disabled as an identity provider, click the button Enable Identity Provider.
Tip
After making changes in Identity Provider Setup, you may need to refresh the page.
-
2. Create a connected app in Salesforce
Follow these steps to configure a Connected App in Salesforce and obtain the Salesforce Consumer Key (Client ID) and Salesforce Consumer Secret (Client Secret):
-
If you are continuing from Enable Salesforce as an identity provider, on the same screen, in the section Service Providers, click the link to create via Connected Apps. Otherwise, navigate to Setup > Build > Create > Apps and click New under the Connected Apps section.
-
Under Basic Information, provide a Connected App Name (for example, Jitterbit API Manager APIs) and populate other required fields.
-
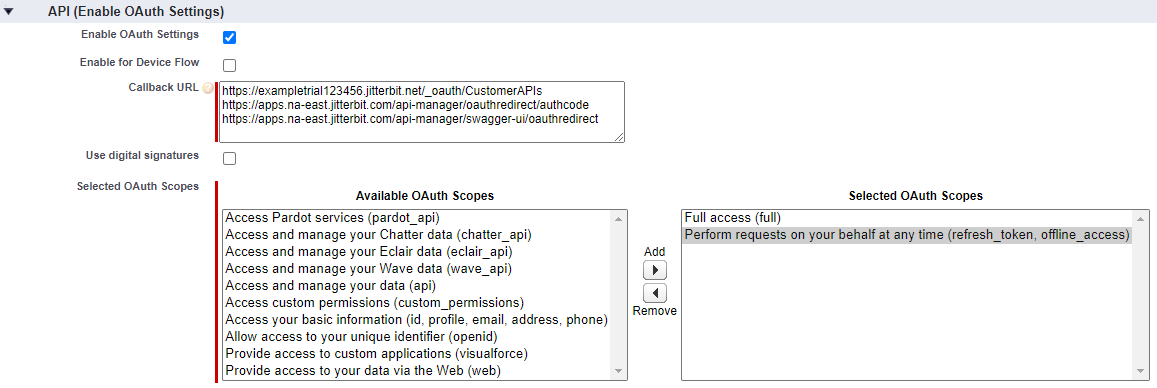
Under API (Enable OAuth Settings), select Enable OAuth Settings. This enables the additional fields Callback URL and Selected OAuth Scopes:
-
Callback URL: Enter the URLs appropriate for your Harmony organization and region:
-
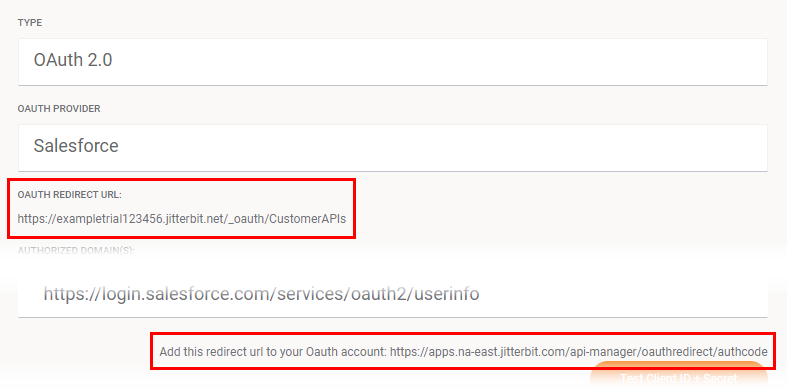
Enter the two URL values copied from the security profile configuration screen (the image below is cropped to show the relevant areas):
-
Enter the URL value appropriate for your region (see Finding my region):
- NA:
https://apps.na-east.jitterbit.com/api-manager/swagger-ui/oauthredirect - EMEA:
https://apps.emea-west.jitterbit.com/api-manager/swagger-ui/oauthredirect - APAC:
https://apps.apac-southeast.jitterbit.com/api-manager/swagger-ui/oauthredirect - Selected OAuth Scopes: Select these OAuth scopes by moving them to Selected OAuth Scopes:
- NA:
- Full access (full)
- Perform requests on your behalf at any time (refresh_token, offline_access)
-
-
-
On clicking Save, the Consumer Key (equivalent to client ID in API Manager) and Consumer Secret (equivalent to client secret in API Manager) are displayed under API (Enable OAuth Settings). Retain these for later use, as they will be required when configuring the security profile.
3. Configure a security profile in API Manager
Follow the instructions for Configure a security profile in Security profile configuration.
During configuration, select OAuth 2.0 as the authentication Type and Salesforce as the OAuth provider:
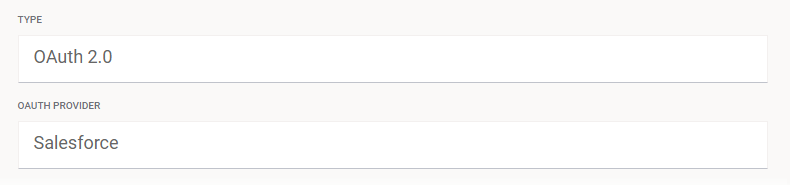
Enter the OAuth client ID (Salesforce Consumer Key) and OAuth client secret (Salesforce Consumer Secret) values obtained in the previous section, Create a connected app in Salesforce:
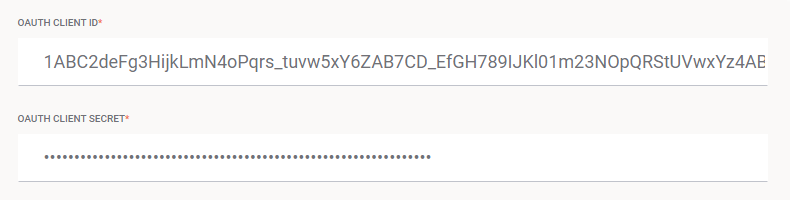
Click Test Client ID + Secret to verify connectivity with the identity provider using the configuration.
4. Assign a security profile in API Manager
To use the security profile with an API, follow the instructions for configuring a custom API, OData service, or proxy API and select the security profile configured with Salesforce OAuth 2.0 authentication.
5. Access an API with Salesforce authentication
Once you have saved and published a custom API, OData service, or proxy API, its API is accessible by URL in the application calling the API using the configured authentication method.
To consume the API, use the link to Copy URL and use it within the calling application:
If the API supports GET, you can also paste the URL into a web browser to consume the API manually.
The browser redirects to the native login interface for Salesforce. Provide your credentials to authenticate with Salesforce.
If the authentication is successful, the expected payload is displayed in the web browser.