Security Profiles page in Jitterbit API Manager
Introduction
This page describes the user interface of the Security Profiles page within API Manager.
To perform actions or make edits on the Security Profiles page, a role with Admin permission is required. Users in roles with Write environment access have read-only access.
For information on security profiles, see Security profiles on API Manager security.
For information on configuring a security profile, see Security profile configuration.
Access the Security Profiles page
The Security Profiles page can be accessed from either the Harmony portal menu or the API Manager navigation menu:
-
Use the Harmony portal menu to select API Manager > Security Profiles:

-
When accessing an API Manager page, use its navigation menu to select Security Profiles:
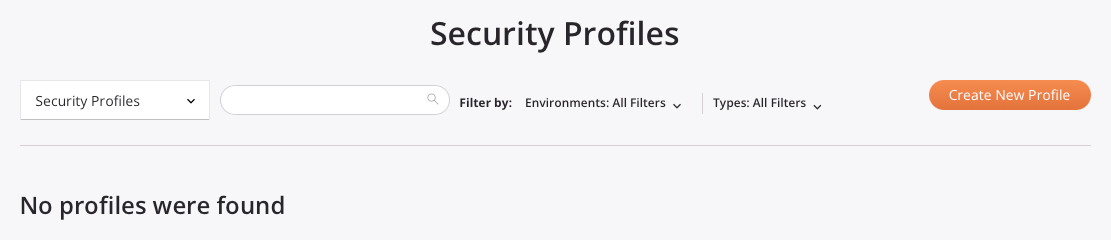
If no security profiles have yet been created in the selected Harmony organization, the Security Profiles page displays a message that no profiles were found.
To create a security profile, click Create New Profile:
Note
Information on configuring a new security profile is provided on Security profile configuration.
Security Profiles page header
The header along the top of the Security Profiles page includes navigation within API Manager, a search box, filters, and a button for creating a new security profile:

- Navigation: Use the API Manager navigation menu to navigate to other pages within API Manager.
- Search: Enter any part of a security profile's name into the search box to filter security profiles by name. The search is not case-sensitive.
- Filter by: You can filter security profiles by environment or authorization type:
- Environments: Use the dropdown to select environments where the security profiles are located. When all filters are unselected, security profiles for all environments in the organization to which you have access are displayed.
- Types: Use the dropdown to select the authorization types of the security profiles (Anonymous, Basic, OAuth 2.0, or API Key). When all filters are unselected, security profiles with any authorization type are displayed.
- Create New Profile: Click to open the security profile configuration screen, where you can create a new security profile (see Security profile configuration).
View existing security profiles
The Security Profiles page displays all existing security profiles in the selected Harmony organization, grouped by environment. Each table column is described below:
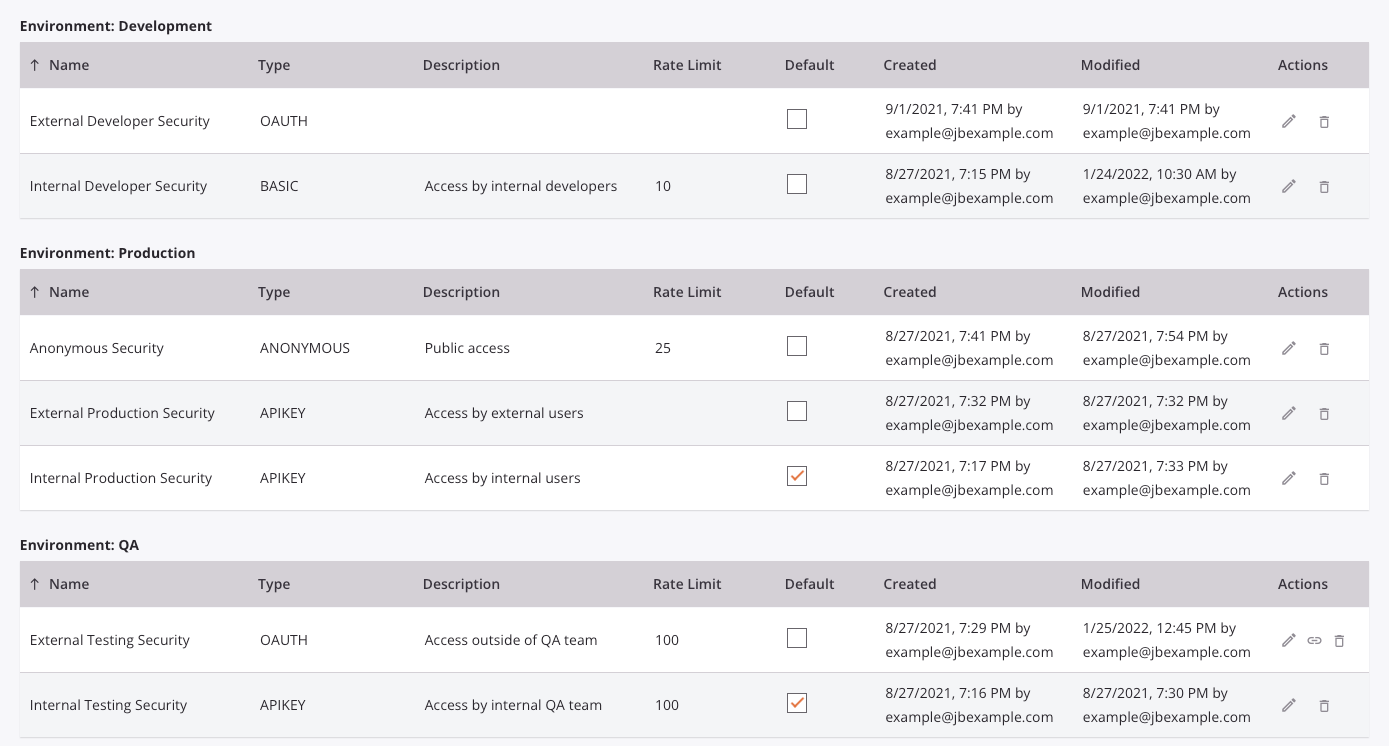
- Name: The name of the security profile. To toggle the sorting order of each table between descending and ascending alphabetical order, click the up or down arrow.
- Type: The authentication type that is used to authenticate with and access the APIs that the security profile is assigned to.
- Description: A description of the security profile, if provided.
- Rate Limit: The maximum number of API hits allowed per minute using the profile, if provided.
- Default: Select to make this security profile the default security profile for the environment. The default security profile will be preselected when a new API is created. Only one default security profile can be selected in each environment. Once a default security profile has been selected, selecting a different default security profile will remove the existing default security profile selection. Selecting or changing the default security profile will not change the security profile assigned to existing APIs.
- Created: The date and local browser time that the security profile was created, and the user who created it.
- Modified: The date and local browser time that the security profile was last modified, and the user who modified it.
- Actions: These actions are available on each security profile:
- Edit: Click to open the security profile configuration screen.
- OAuth display URL: When a 2-legged OAuth security profile is configured, click to copy the URL needed to generate an OAuth token. Refer to the instructions for 2-legged Azure AD or 2-legged Okta.
- Delete: Click to permanently delete the security profile. A message asks you to confirm that you want to delete the security profile. If the security profile is assigned to any APIs, it must first be unassigned or replaced prior to deleting it.
Next steps
For information on configuring a security profile, see Security profile configuration.
For more information on assigning security profiles to an API, see these resources: