Configure duo single sign-on with SAML as a security provider in Jitterbit App Builder
This article steps through how to configure Duo Single Sign-On with SAML as an SSO Security Provider in App Builder. The Duo Single Sign-On configuration needs to be set up first, followed by configuring the App Builder Security Provider information to connect to Duo Single Sign-On.
Duo single sign-on with SAML
Duo Single Sign-On offers a SAML-based service that provides companies with control over the authorization and authentication of hosted user accounts that can access web-based entities. App Builder acts as the identify provider and, when configured along with Duo Single Sign-On, can be used to authenticate and authorize Users into an App Builder app.
Before configuring Duo Single Sign-On for use with App Builder, you will need to enable Duo Single Sign-On for your Duo account and configure an authentication source. See the Duo Single Sign-On for Generic SAML Service Providers article for guidance.
The Duo Single Sign-On service is based on the SAML v2.0 specifications.
Duo single sign-on configuration settings
To get started, configure Duo Single Sign-On for use with your {{nm.ab}} app:
- Log into the Duo Admin Panel
- Go to Applications
- Click Protect an Application and locate the Generic SAML Service Provider with protection type
2FA with SSO hosted by Duo (Single Sign-On)in the applications list - Click Protect to start configuring the Generic SAML Service Provider
-
On the Generic SAML Service Provider page you will need to reference some of the Metadata and Downloads values for the {{nm.ab}} configuration:
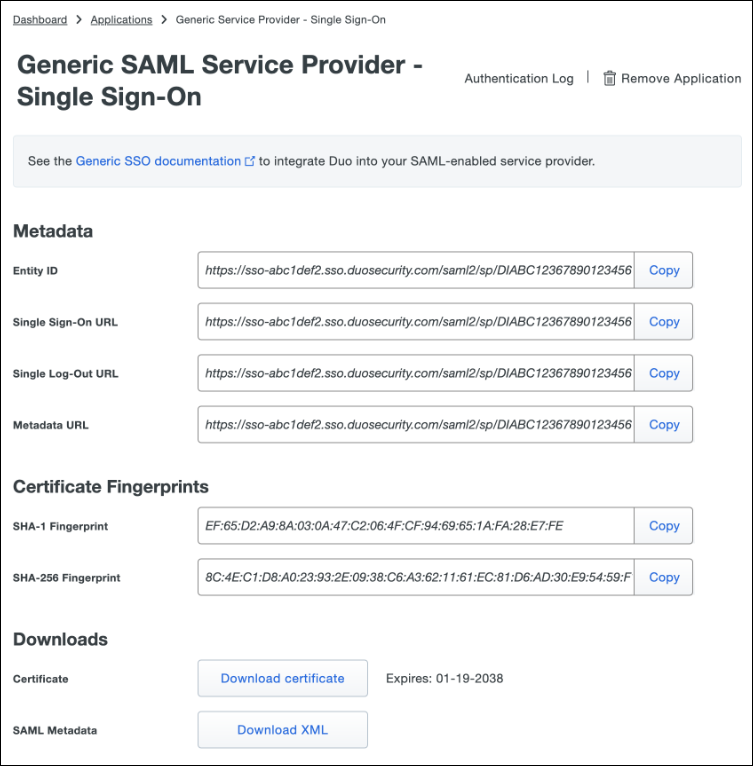
-
Copy the Metadata URL and download the Certificate
-
In the Service Provider section, enter the following information:
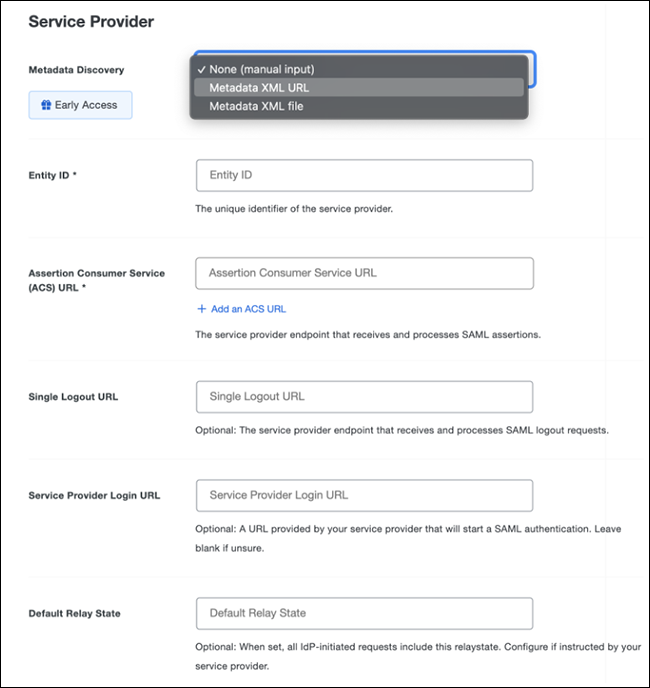
- Metadata Discovery: None (manual input)
- Entity ID: Corresponds with Sign In Provider URL. Example:
https://example.zudy.com/signin-{{ProviderName}} - ACS URL: The URL where your service provider receives SAML assertions. This will be the same value as your Entity ID.
App Builder security provider
After the Duo Single Sign-On configuration is complete, you will configure Duo in App Builder as a SAML Security Provider.
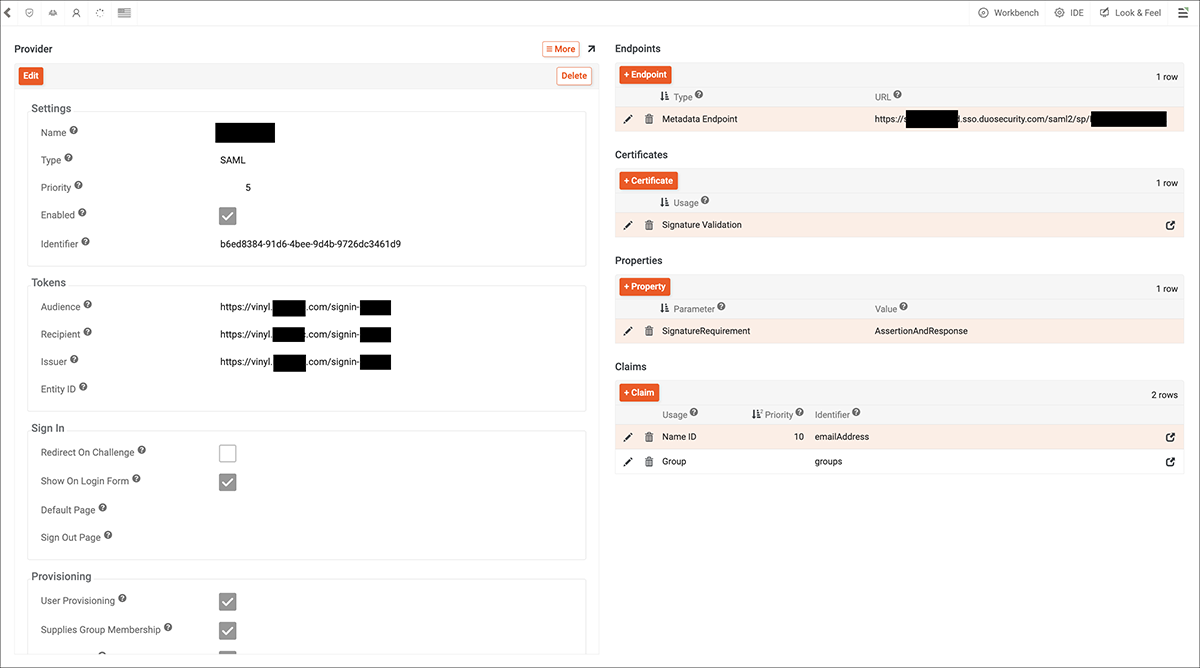
Duo Single Sign-On SAML Provider configuration example
App Builder configuration specific to duo single sign-on
Follow the basic configuration for App Builder as a SAML security provider. In addition, review and confirm the following settings which are specific to integration with Duo Single Sign-On:
Settings
- Name: Duo Single Sign-On
- Type: SAML
- Enabled: True
Tokens
- Audience, Recipient, and Issuer: values must match the Entity ID value provided from Duo Single Sign-On. Example:
https://vinyl.example.com/signin-Duo
Endpoints
- Metadata Endpoint: value must match the Metadata URL value provided from Duo Single Sign-On. Example:
https://example.sso.duosecurity.com/saml2/sp/12345
Properties
- SignatureRequirement: value set to AssertionAndResponse.
Claims
- Configure Claims records to instruct how to handle the identity creation and group mapping. Example: Name ID is a Usage type, with emailAddress as the Identifier value. You may also configure Group as a Usage type, with groups as the Identifier.
Lastly you will need to upload the Certificate information downloaded from Duo Single Sign-On:
- Click + Certificate from the Certificates area on Provider settings
- Select Signature Validation for Usage
- Select X.509 Certificate for Type
- Select PEM for Format
- Enter the Duo Security Certificate information. Be sure to remove the start and end notation from the certificate.