Elasticsearch Get Index activity¶
Introduction¶
An Elasticsearch Get Index activity, using its Elasticsearch connection, retrieves a list of indices from Elasticsearch and is intended to be used as a source in an operation.
Note
If the Elasticsearch security features are enabled in your Elasticsearch instance, you must have the view_index_metadata or manage index privilege for the target index or index alias.
Create an Elasticsearch Get Index activity¶
An instance of an Elasticsearch Get Index activity is created from an Elasticsearch connection using its Get Index activity type.
To create an instance of an activity, drag the activity type to the design canvas or copy the activity type and paste it on the design canvas. For details, see Creating an activity instance in Component reuse.
An existing Elasticsearch Get Index activity can be edited from these locations:
- The design canvas (see Component actions menu in Design canvas).
- The project pane's Components tab (see Component actions menu in Project pane Components tab).
Configure an Elasticsearch Get Index activity¶
Follow these steps to configure an Elasticsearch Get Index activity:
- Step 1: Enter a name
Provide a name for the activity. - Step 2: Review the data schemas
Any request or response schemas generated from the endpoint are displayed.
Step 1: Enter a name¶
In this step, provide a name for the activity:
-
Name: Enter a name to identify the activity. The name must be unique for each Elasticsearch Get Index activity and must not contain forward slashes (
/) or colons (:). -
Save & Exit: If enabled, click to save the configuration for this step and close the activity configuration.
-
Next: Click to temporarily store the configuration for this step and continue to the next step. The configuration will not be saved until you click the Finished button on the last step.
-
Discard Changes: After making changes, click to close the configuration without saving changes made to any step. A message asks you to confirm that you want to discard changes.
Step 2: Review the data schemas¶
Any request or response schemas generated from the endpoint are displayed:
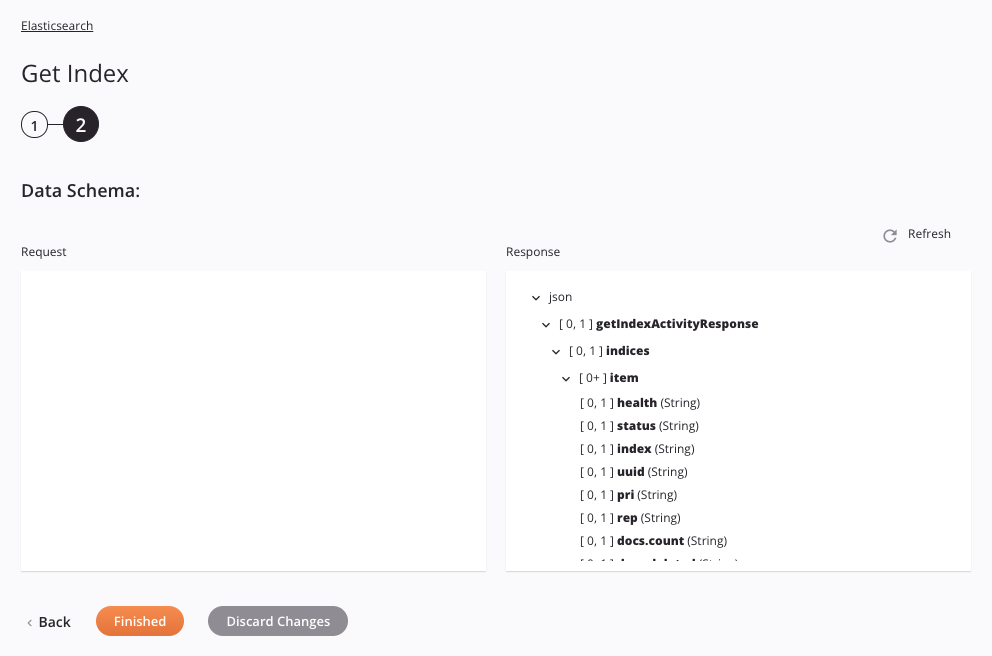
- Data Schemas: These data schemas are inherited by adjacent transformations and are displayed again during transformation mapping.
!!! note Data supplied in a transformation takes precedence over the activity configuration.
The Elasticsearch connector uses the Elasticsearch REST API 7.14.1. Refer to the API documentation for information on the schema nodes and fields.
The data schema consists of these nodes and fields:
| Response Schema Node/Field | Description |
|---|---|
| indices | Indices |
| item | Item |
| health | Health status used to limit returned indices |
| status | Status of the index |
| index | The name of the index |
| uuid | UUID value |
| pri | Primary shards value |
| rep | Rep |
| docs.count | Number of documents in the index |
| docs.deleted | Number of documents deleted from the index |
| store.size | Store size of primary and replica shards |
| pri.store.size | Store size of primary shards |
-
Refresh: Click the refresh icon
 or the word Refresh to regenerate schemas from the Elasticsearch endpoint. This action also regenerates a schema in other locations throughout the project where the same schema is referenced, such as in an adjacent transformation.
or the word Refresh to regenerate schemas from the Elasticsearch endpoint. This action also regenerates a schema in other locations throughout the project where the same schema is referenced, such as in an adjacent transformation. -
Back: Click to temporarily store the configuration for this step and return to the previous step.
-
Finished: Click to save the configuration for all steps and close the activity configuration.
-
Discard Changes: After making changes, click to close the configuration without saving changes made to any step. A message asks you to confirm that you want to discard changes.
Next steps¶
After configuring an Elasticsearch Get Index activity, complete the configuration of the operation by adding and configuring other activities, transformations, or scripts as operation steps. You can also configure the operation settings, which include the ability to chain operations together that are in the same or different workflows.
Menu actions for an activity are accessible from the project pane and the design canvas. For details, see Activity actions menu in Connector basics.
Elasticsearch Get Index activities can be used as a source with these operation patterns:
- Transformation pattern
- Two-target archive pattern (as the first source only)
- Two-target HTTP archive pattern (as the first source only)
- Two-transformation pattern (as the first source only)
To use the activity with scripting functions, write the data to a temporary location and then use that temporary location in the scripting function.
When ready, deploy and run the operation and validate behavior by checking the operation logs.