JWT (Beta) Generate Token activity¶
Introduction¶
A JWT (Beta) Generate Token activity, using its JWT (beta) connection, generates a JSON Web Token (JWT) and is intended to be used as a target to consume data in an operation.
Note
This connector is currently released as a beta version and is available only to select organizations. To participate in the beta program or provide feedback on bugs and enhancements, contact your Customer Success Manager (CSM).
Create a JWT (Beta) Generate Token activity¶
An instance of a JWT (Beta) Generate Token activity is created from a JWT (beta) connection using its Generate Token activity type.
To create an instance of an activity, drag the activity type to the design canvas or copy the activity type and paste it on the design canvas. For details, see Creating an activity instance in Component reuse.
An existing JWT (Beta) Generate Token activity can be edited from these locations:
- The design canvas (see Component actions menu in Design canvas).
- The project pane's Components tab (see Component actions menu in Project pane Components tab).
Configure a JWT (Beta) Generate Token activity¶
Follow these steps to configure a JWT (Beta) Generate Token activity:
-
Step 1: Enter a name and specify settings
Provide a name for the activity and specify the JWT type, JWT type-dependent settings, and optional settings. -
Step 2: Review the data schemas
Any request or response schemas are displayed.
Step 1: Enter a name and specify settings¶
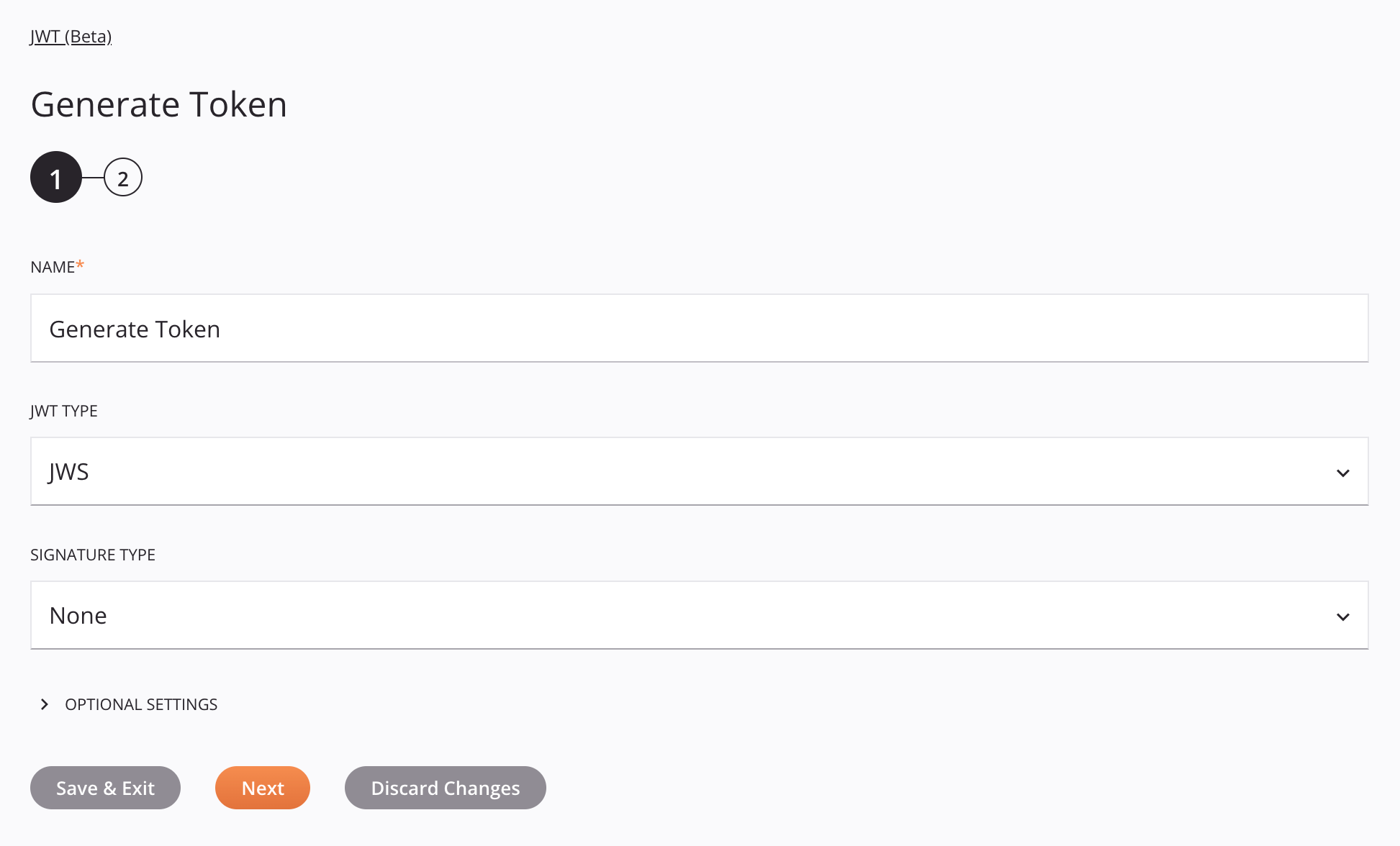
In this step, provide a name for the activity and specify the JWT type, JWT type-dependent settings, and optional settings. Each user interface element of this step is described below.
Tip
Fields with a variable icon support using global variables, project variables, and Jitterbit variables. Begin either by typing an open square bracket [ into the field or by clicking the variable icon to display a list of the existing variables to choose from.
-
Name: Enter a name to identify the activity. The name must be unique for each JWT (Beta) Generate Token activity and must not contain forward slashes
/or colons:. -
JWT Type: Select between signing the JWT using a JSON Web Signature (JWS) or encrypting it using JSON Web Encryption (JWE).
Important
If signatures or encryption are not required, select the JWS JWT type and the None signature type.
-
JWE: If using the JWE JWT type:
-
Key Management Algorithm Type: One of Asymmetric or Symmetric.
-
Asymmetric: If using the Asymmetric key management algorithm type:
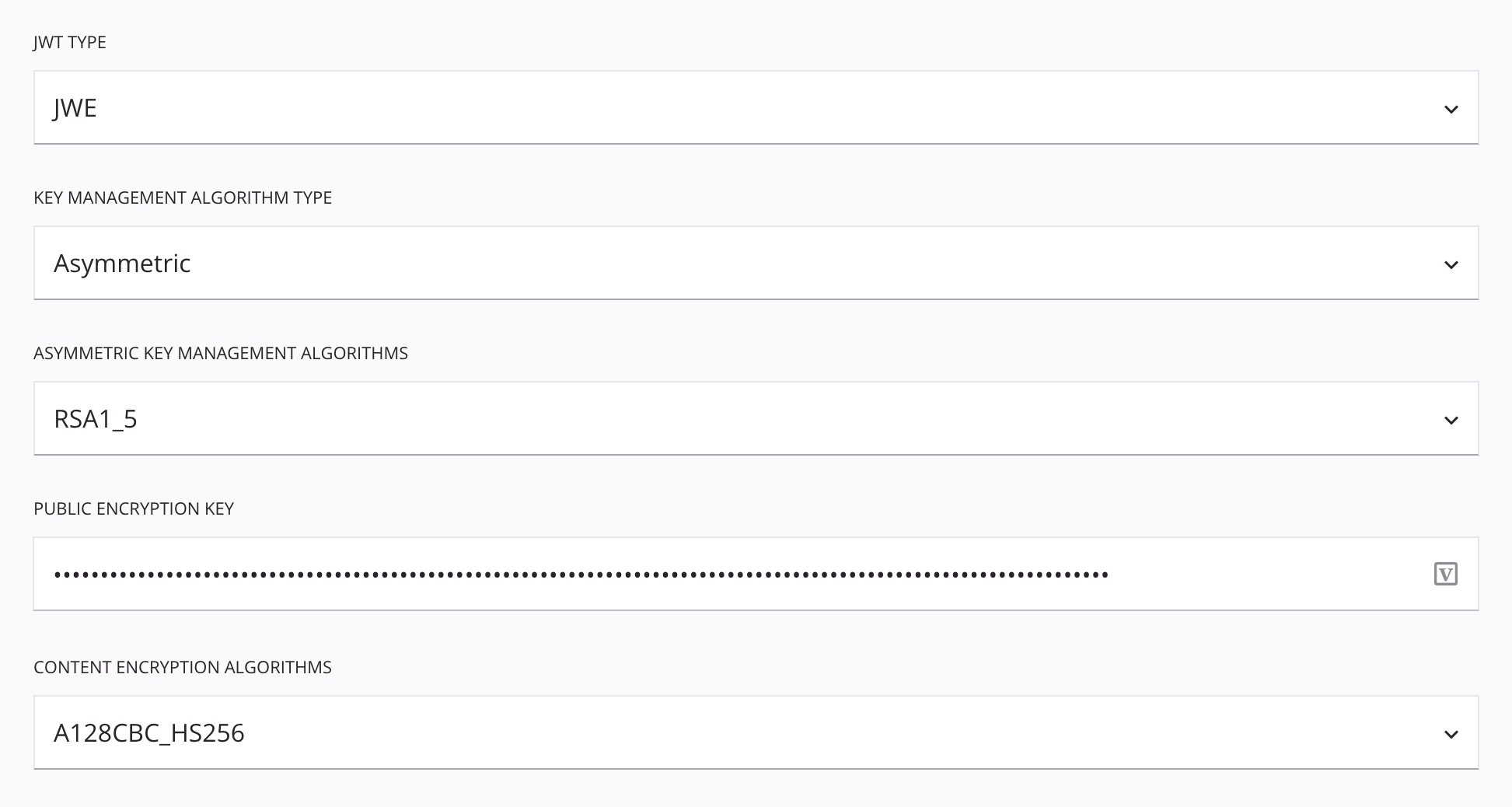
- Asymmetric Key Management Algorithms: One of RSA1_5, RSA_OAEP, or RSA_OAEP_256.
- Public Encryption Key: Enter a public key.
-
Symmetric: If using the Symmetric key management algorithm type:
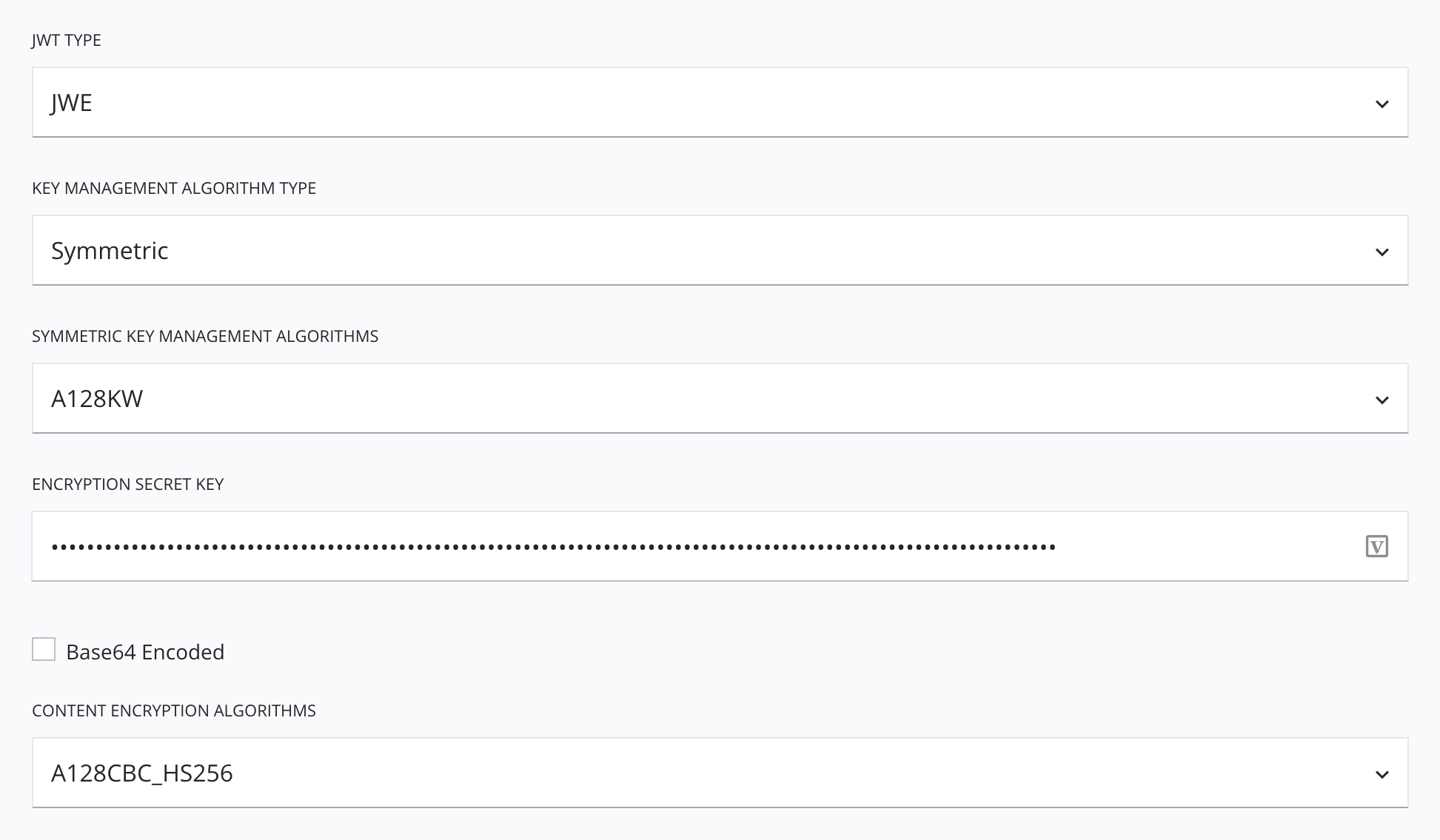
- Symmetric Key Management Algorithms: One of A128KW, A192KW, or A256KW.
- Encryption Secret Key: Enter a secret key.
- Base64 Encoded: Select if Base64 encoding is required.
-
-
Content Encryption Algorithms: One of A128CBC_HS256, A128GCM, A192CBC_HS384, A192GCM, A256CBC_HS512, or A256GCM.
-
-
JWS: If using the JWS JWT type:
-
Signature Type: One of Asymmetric, Symmetric, or None.
-
Asymmetric: If using the Asymmetric signature yype:
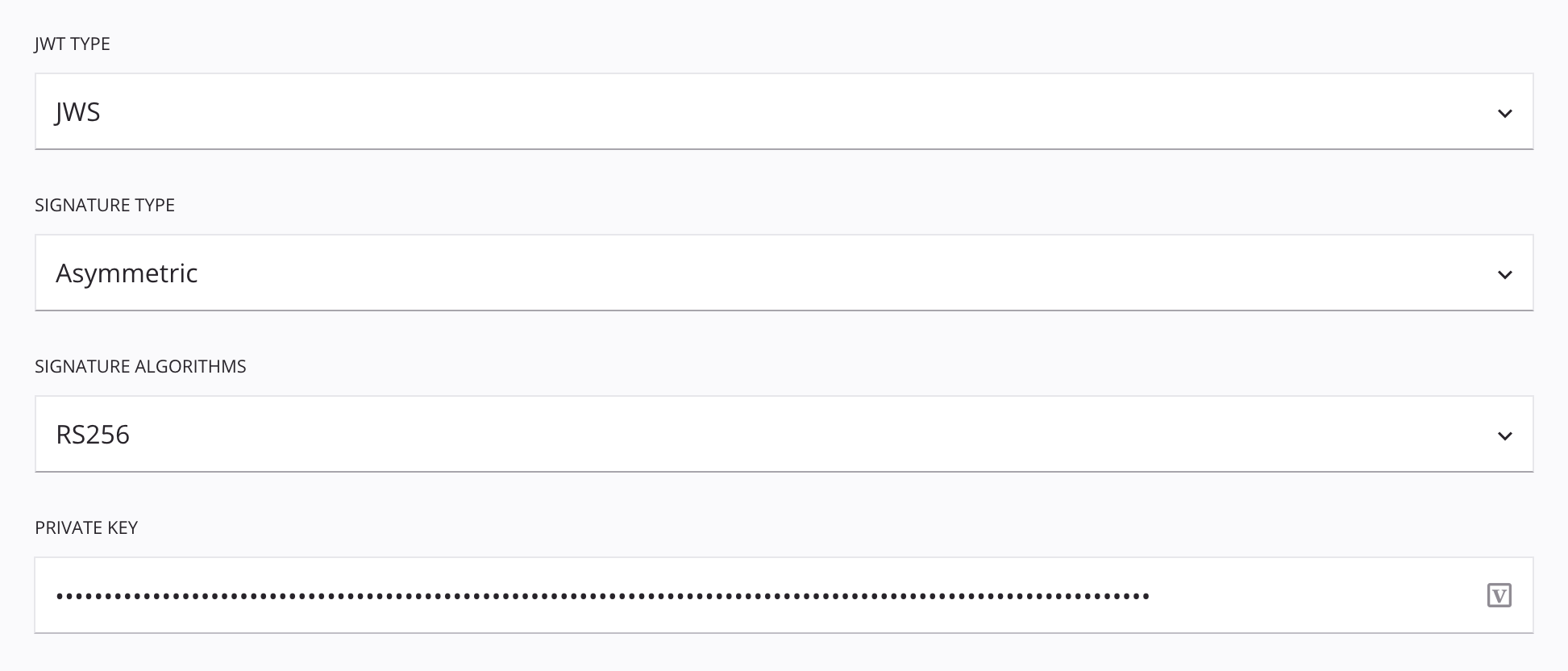
- Signature Algorithms: One of ES256, ES384, ES512, PS256, PS384, PS512, RS256, RS384, or RS512.
- Private Key: Enter a private key.
-
Symmetric: If using the Symmetric signature type:
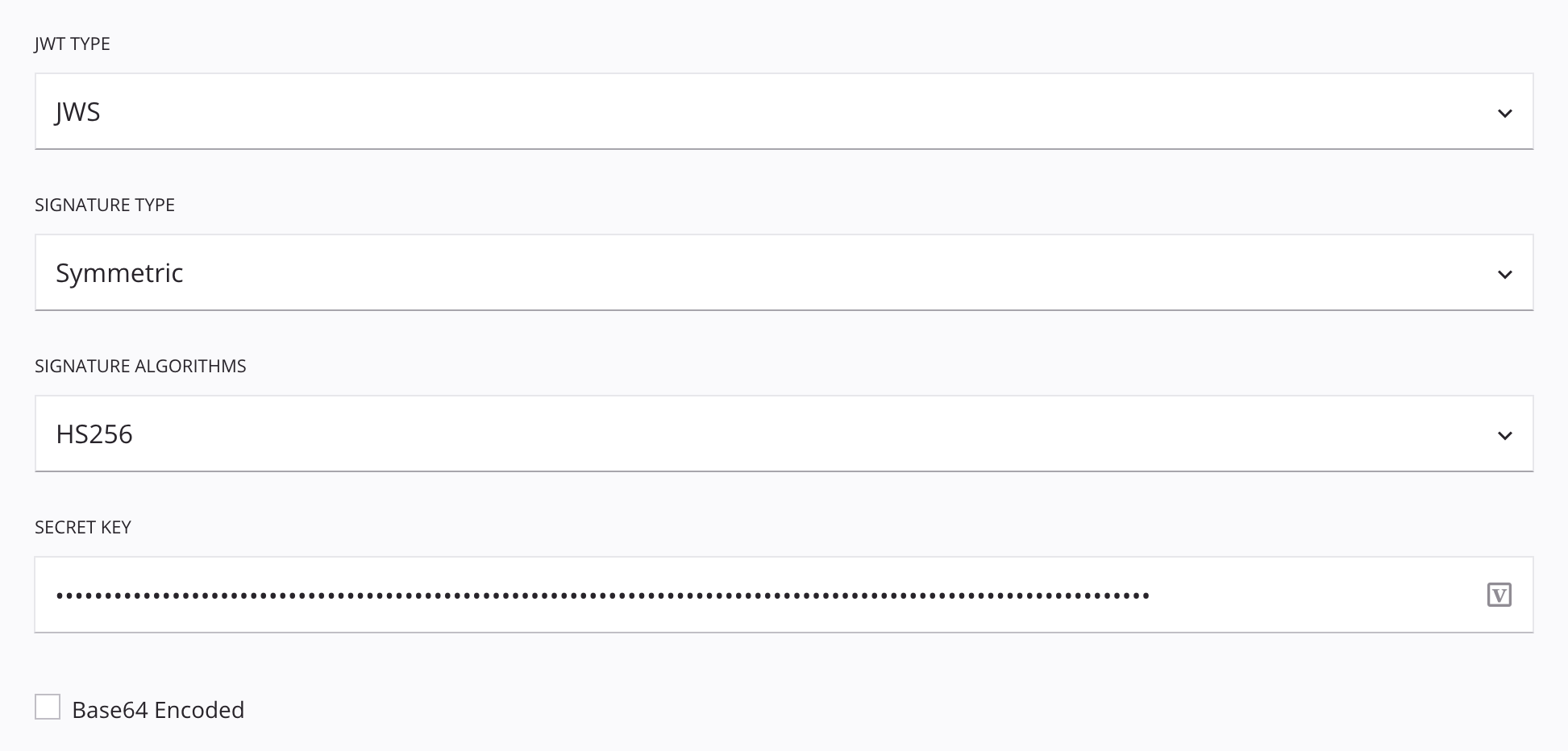
- Signature Algorithms: One of HS256, HS384, or HS512.
- Secret Key: Enter a secret key.
- Base64 Encoded: Select if Base64 encoding is required.
-
None: If using the None signature type, no additional fields appear.
-
-
-
-
Optional Settings: Click to expand additional optional settings:
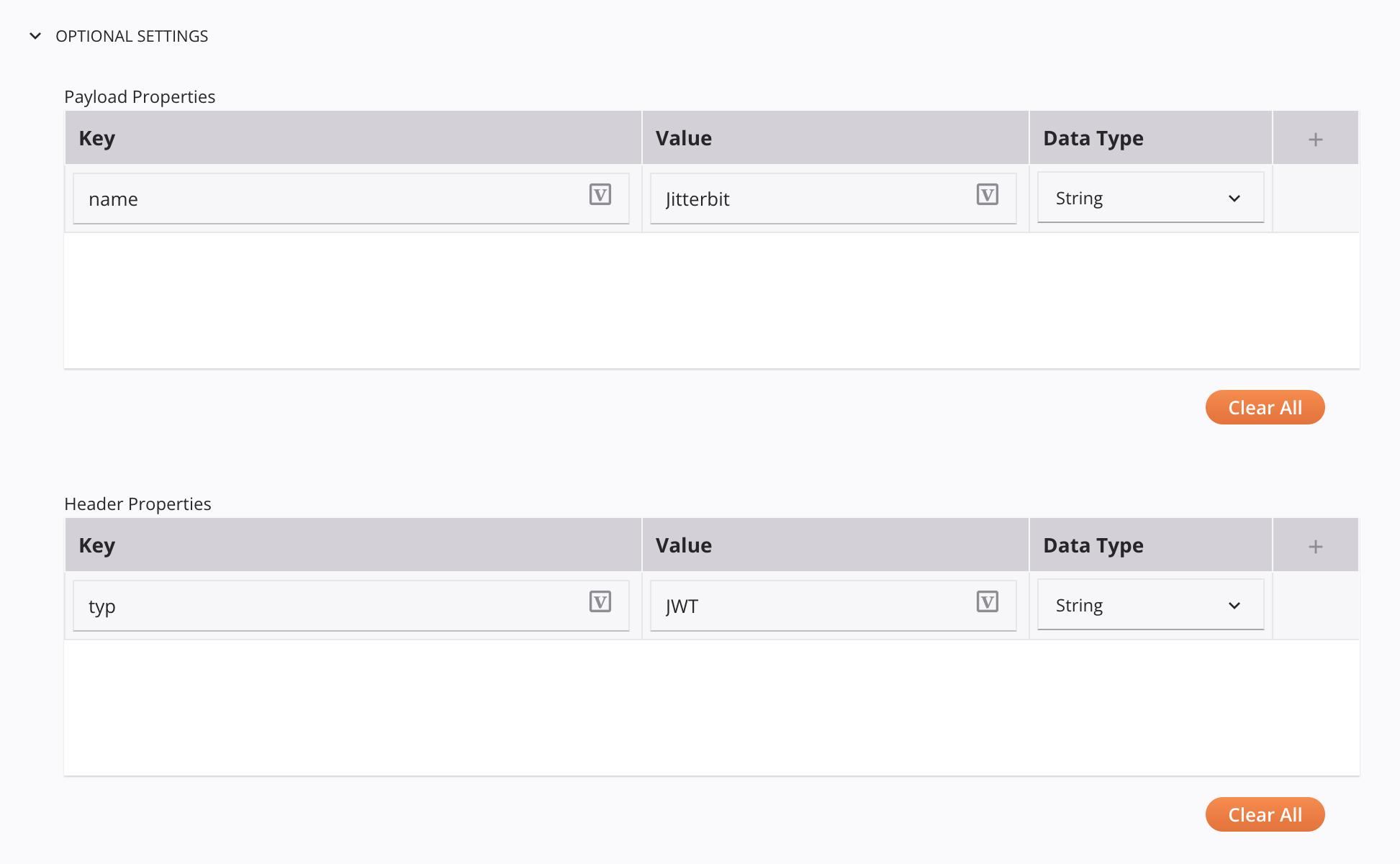
- Payload Properties: The JWT payload.
- Header Properties: Metadata relevant to the JWT payload.
-
Save & Exit: If enabled, click to save the configuration for this step and close the activity configuration.
-
Next: Click to temporarily store the configuration for this step and continue to the next step. The configuration will not be saved until you click the Finished button on the last step.
-
Discard Changes: After making changes, click to close the configuration without saving changes made to any step. A message asks you to confirm that you want to discard changes.
Step 2: Review the data schemas¶
Any request or response schemas are displayed. Each user interface element of this step is described below.
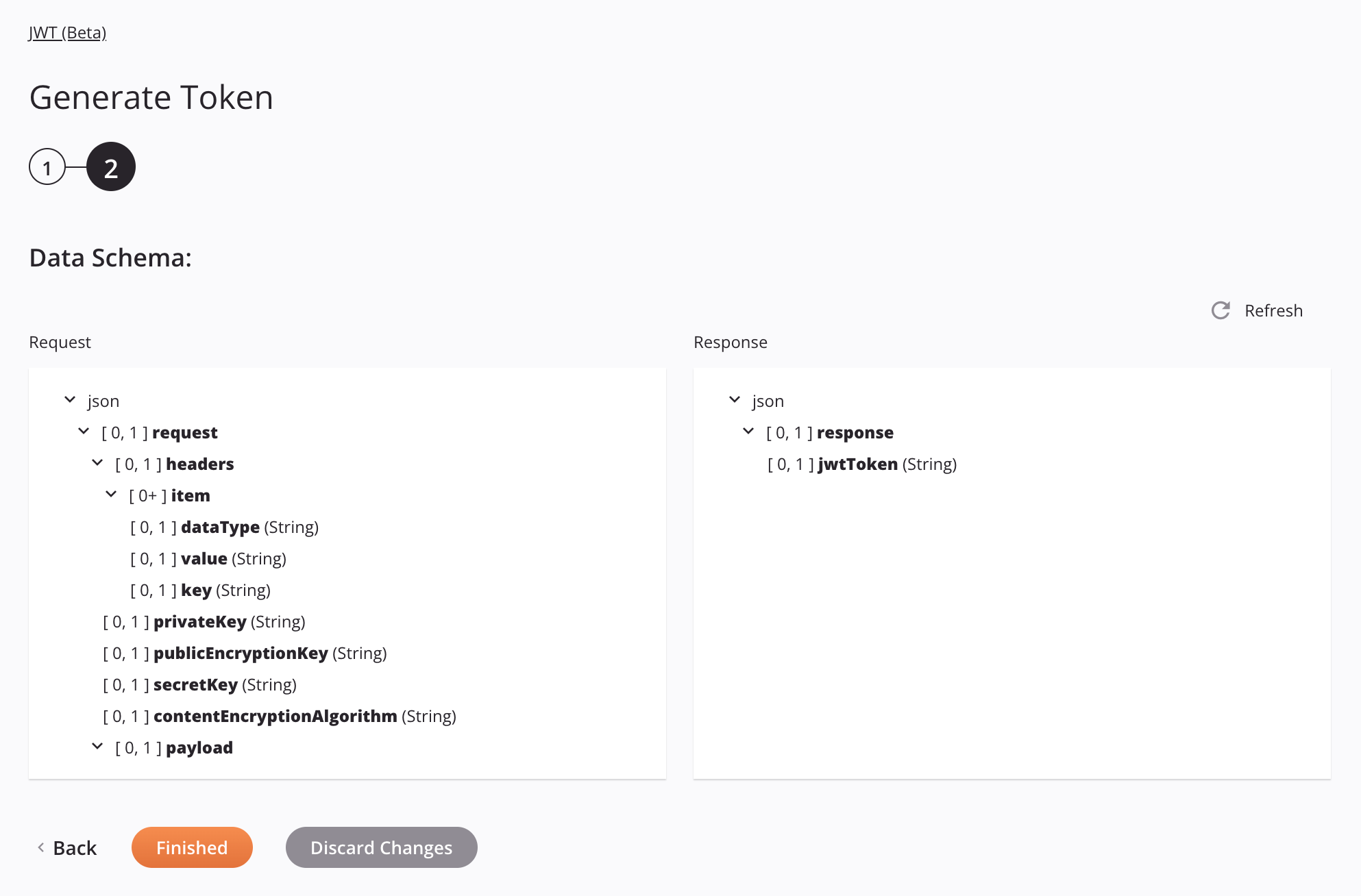
-
Data Schemas: These data schemas are inherited by adjacent transformations and are displayed again during transformation mapping.
Note
Data supplied in a transformation takes precedence over the activity configuration.
The JWT (Beta) connector uses the Java JWT. The schema nodes and fields are based on the selections made in step 1.
-
Refresh: Click the refresh icon or the word Refresh to regenerate schemas from the JWT (Beta) endpoint. This action also regenerates a schema in other locations throughout the project where the same schema is referenced, such as in an adjacent transformation.
-
Back: Click to temporarily store the configuration for this step and return to the previous step.
-
Finished: Click to save the configuration for all steps and close the activity configuration.
-
Discard Changes: After making changes, click to close the configuration without saving changes made to any step. A message asks you to confirm that you want to discard changes.
Next steps¶
After configuring a JWT (Beta) Generate Token activity, complete the configuration of the operation by adding and configuring other activities, transformations, or scripts as operation steps. You can also configure the operation settings, which include the ability to chain operations together that are in the same or different workflows.
Menu actions for an activity are accessible from the project pane and the design canvas. For details, see Activity actions menu in Connector basics.
JWT (Beta) Generate Token activities can be used as a target with these operation patterns:
- Transformation pattern
- Two-transformation pattern (as the first or second target)
To use the activity with scripting functions, write the data to a temporary location and then use that temporary location in the scripting function.
When ready, deploy and run the operation and validate behavior by checking the operation logs.