Mitigate the Apache Log4j2 JNDI vulnerability in Jitterbit Harmony
Summary
This page summarizes the Apache Log4j2 vulnerabilities, describes their impact on Jitterbit products, and explains how the vulnerabilities were mitigated.
Discovery of vulnerabilities
On 9 December 2021, a Critical Zero-Day vulnerability was disclosed by Apache that affects Apache Log4j2 (CVE-2021-44228). An additional related vulnerability was disclosed by Apache on 14 December 2021 (CVE-2021-45046).
Mitigation for private agents
On 16 December 2021, Jitterbit performed an emergency maintenance to address the Apache Log4j2 vulnerabilities.
After the conclusion of the maintenance on 16 December 2021 at 5 pm PST (17 December 2021 12 pm AEDT; 17 December 2021 2 am CET; 2021‑12‑17 01:00 UTC), you must perform the following steps in order for the update to become effective:
- On each private agent, you must manually delete all JAR files from
<JITTERBIT_HOME>/Connectors. (The exception would be any JAR files for connectors that you have installed locally.) - Each private agent must be restarted.
- Run an operation where each connector is used or test each connection for each connector JAR on the agent.
If you have not performed all of the above steps in this order after completion of the maintenance, do so immediately to protect your organization from these vulnerabilities.
A previous version of this page instructed users only to restart private agents. Restarting private agents is effective for most connectors. However, for some connectors it is necessary to perform all steps. We recommend deleting all JAR files in the Connectors directory to ensure you are protected from these vulnerabilities. You can verify you are protected by searching for log4j in any filenames and checking the Log4j version as described below.
Previous workaround for private agents
Prior to 16 December 2021, a workaround to manually address the vulnerabilities was previously published on this page prior to the emergency maintenance. This workaround is no longer required for any private agent versions.
If you have already performed the workaround, you do not need to reverse it. If you have not restarted private agents since the emergency maintenance was completed, you should restart the agents so they receive the emergency maintenance update. No additional action beyond restarting is recommended with regard to these vulnerabilities.
What are the Apache Log 4j2 JNDI vulnerabilities?
From the NIST National Vulnerability Database CVE-2021-44228:
Apache Log4j2 \<=2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From Log4j 2.15.0, this behavior has been disabled by default.
A related vulnerability is CVE-2021-45046, which describes a vulnerability in the Log4j 2.15.0 library. Both of these vulnerabilities are covered and addressed here.
Which Jitterbit products were impacted by the vulnerabilities?
These vulnerabilities were limited to Integration Studio connectors created with the Integration Studio Connector SDK ("Integration Studio Connector SDK connectors").
As connectors are not typically considered to be standalone Jitterbit products and must be run on a Jitterbit agent, some explanation is necessary to explain the impact and mitigation steps to address these vulnerabilities:
- What Is an Integration Studio Connector SDK Connector?
Integration Studio Connector SDK connectors are connectors built with the Integration Studio Connector SDK. They currently include certain connectors built by Jitterbit or by a third party:- Jitterbit: Most of the current Integration Studio application connectors were created using the Connector SDK. Exceptions include the NetSuite, Salesforce, Salesforce Service Cloud, SAP, and ServiceMax connectors, which were not created using the Connector SDK and are not affected. See the complete list below of the Jitterbit connectors affected by these vulnerabilities. Future connectors created by Jitterbit using the Connector SDK will not be affected.
- Third-party: As the Connector SDK is publicly available for creating Integration Studio connectors, your organization may be using additional connectors created with the Connector SDK by a partner or third party and may also be affected by these vulnerabilities. Please contact the provider of that connector to determine if they have evaluated and, if necessary, corrected their connector.
- How Are These Connectors Related to Agents?
The latest version of an Integration Studio Connector SDK connector is downloaded by a Jitterbit agent as needed from Harmony when you use the connector. - What Agents Were Affected?
Any cloud or private agent that was using an Integration Studio Connector SDK connector was impacted by the vulnerabilities, as the Apache Log4j2 library was downloaded and used on the agent to write logs when the connector was being used.- Cloud agents: On cloud agents, Jitterbit immediately addressed these vulnerabilities through appropriate security controls. No further actions are necessary.
- Private agents: On private agents, prior to the emergency maintenance on 16 December 2021, customers were instructed to follow the previously documented workaround to address these vulnerabilities.
These Jitterbit products were not affected:
- Agents That Have Never Used an Integration Studio Connector SDK Connector: Not affected.
- Jitterbit Design Studio (and Its Connectors): Not affected.
- Jitterbit Harmony Cloud: Not affected.
- Jitterbit eiCloud: Not affected.
Jitterbit Integration Studio Connector SDK connectors
The following is a list of all Integration Studio connectors as of 16 December 2021 that have been created by Jitterbit with the Integration Studio Connector SDK and are affected by the Apache Log4j vulnerabilities.
As the Connector SDK is publicly available to developers, your organization may be using a connector not listed here that was created by a partner or third-party using the Integration Studio Connector SDK. Those connectors may also be affected by the Apache Log4j vulnerabilities. Please contact the provider of that connector to find out if they have evaluated and, if necessary, corrected their connector.
What did the 16 December 2021 maintenance do?
On 16 December 2021, Jitterbit performed an emergency maintenance to address the Apache Log4j2 vulnerabilities.
As part of the maintenance, Jitterbit updated the Integration Studio connectors built with the Connector SDK to use an available version of the Log4j library that addressed the two Apache Log4j vulnerabilities.
After the conclusion of the maintenance on 16 December 2021 at 5 pm PST (17 December 2021 12 pm AEDT; 17 December 2021 2 am CET; 2021‑12‑17 01:00 UTC), you must perform the following steps in order for the update to become effective:
- On each private agent, you must manually delete all JAR files from
<JITTERBIT_HOME>/Connectors. (The exception would be any JAR files for connectors that you have installed locally.) - Each private agent must be restarted.
- Run an operation where the connector is used or test the connection.
If you have not performed all of the above steps in this order after completion of the maintenance, do so immediately to protect your organization from these vulnerabilities.
A previous version of this page instructed users only to restart private agents. Restarting private agents is effective for most connectors. However, for some connectors it is necessary to perform all steps. We recommend deleting all JAR files in the Connectors directory to ensure you are protected from these vulnerabilities. You can verify you are protected by searching for log4j in any filenames and checking the Log4j version as described below.
How Can I Confirm Protection from These Vulnerabilities?
Once implementing the mitigation steps for private agents, you can confirm you are protected by searching the agent installation subdirectories for filenames that include log4j.
Any earlier filenames that include log4j and a version 2 series number, such as log4j-api-2.11.1.jar, should no longer be present. Any Log4j version 2 series filenames should now be replaced with a name indicating the version is at least 2.16.0.
For further assistance, contact Jitterbit support.
Previous Workaround for private agents
This workaround was previously published prior to the emergency maintenance on 16 December 2021. This workaround is no longer needed and the vulnerabilities are addressed with an agent restart after the 16 December 2021 maintenance. If you have already performed this workaround and restarted private agents, no further action is needed.
For customers with private agents, the following steps were previously recommended to protect against the Apache Log4j vulnerabilities.
Caution
- It is best practice to have private agents behind a firewall with no inbound ports. This protects against inbound exploits.
- These settings will be overwritten when updating or upgrading.
Linux private agent
For Linux private agents, the manual workaround is to edit the startup script for the Tomcat server.
The file to change is catalina.sh, located at <JITTERBIT_HOME>/tomcat/bin/catalina.sh. On a typical installation, this will be located at this location:
/opt/jitterbit/tomcat/bin/catalina.sh
-
Add the following line immediately after the comment lines at the beginning of the file:
JAVA_OPTS="$JAVA_OPTS -Dlog4j2.formatMsgNoLookups=true" -
For example:
. . . # case the default is "true" # ----------------------------------------------------------------------------- JAVA_OPTS="$JAVA_OPTS -Dlog4j2.formatMsgNoLookups=true" # OS specific support. $var _must_ be set to either true or false. . . . -
Save the change to the file and exit your editor.
-
Restart the private agent:
> jitterbit stop > jitterbit start
Verification of the Change
To verify the results of this change, run the command ps -ef | grep java and look in the output for -Dlog4j2.formatMsgNoLookups=true.
Windows private agent
For Windows private agents, you will need to edit the registry.
Caution
Changing the Windows registry incorrectly may affect the Windows Operating System. Please take caution when making these changes.
Follow these steps:
-
Stop the Windows private agent.
-
Use Windows Search to find
regeditand use it to open the Registry Editor. -
Navigate to
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Apache Software Foundation\Procrun 2.0\Jitterbit Tomcat Server\Parameters\Java. -
Modify its Options and add the following before the
-Xmsline:-Dlog4j2.formatMsgNoLookups=trueExample:

-
Exit the Registry Editor.
-
Restart the Windows private agent.
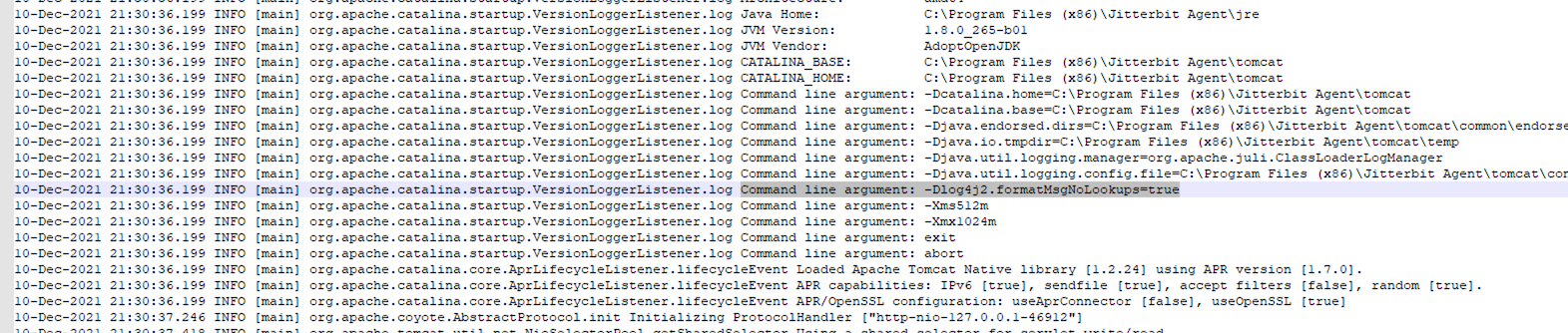
Verification of the Change
To verify the results of this change:
-
Open Notepad (or similar editor).
-
Open the most recent log file, located at:
<JITTERBIT_HOME>\tomcat\logs\catalina.{date}.log -
Search for
-Dlog4j2.formatMsgNoLookups=trueto verify that the command line argument is being used.
Example Verification Output